Mikhail Vasiliev was found involved in extortion for $100 million
Russian-Canadian citizen Mikhail Vasiliev was sentenced to four years in prison by an Ontario court for distributing ransomware LockBit.
Let us recall that 34-year-old Vasiliev was arrested back in November 2022 in Canada, and in February 2024 he pleaded guilty to eight counts, including cyber extortion, criminal damage and weapons crimes committed in 2021 and 2022. He is known to have attacked at least three organizations in Canada, encrypting their data and demanding ransom.
Prosecutors considered him one of LockBit’s key operators and “one of the most active ransomware operators in the world” who was involved in many high-profile hacks. In particular, Vasiliev is believed to be involved in approximately 1,000 cyberattacks that LockBit was behind, resulting in over $100 million in ransom requests.
In 2022, Europol reported that the LockBit operator “was a high priority target” for law enforcement and “distinguished itself” by attempting to extort ransoms ranging from €5 million to €70 million from victims.
At the trial, Vasiliev’s lawyer stated that he became a cybercriminal only during the pandemic, and now he repents and takes full responsibility for his actions. However, the judge Michelle Furst (Michelle Fuerst) called him a “cyberterrorist,” noting that Vasiliev committed crimes solely out of greed and with cold calculation.
In addition to his prison sentence, Vasilyev was ordered to pay $860,000 in compensation to his Canadian victims. He also now faces extradition to the United States, where he will face additional charges.
The FBI and Britain’s National Crime Agency have closed the LockBit portal
Law enforcement agencies from 11 countries globally stopped the activities of the LockBit hacker group as part of a joint operation called Operation Cronos. A banner has now been posted on the crime group’s website indicating that the portal is under the control of the UK’s National Crime Agency (NCA), working in collaboration with the FBI and an international law enforcement team.
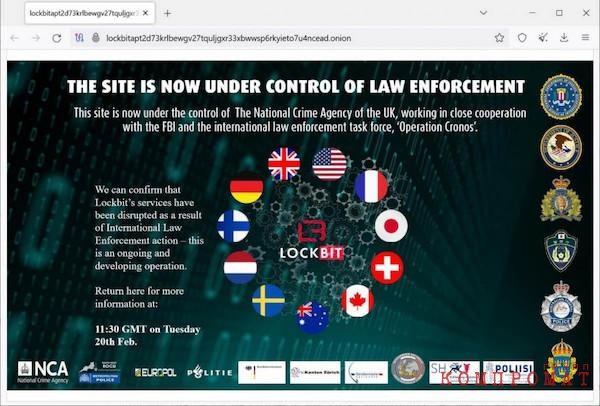 Banner on the LockBit website
Banner on the LockBit websiteAlthough the LockBit site is now down, other grouping portals used to host data and send private messages are still operational. LockBit sites have also stopped opening for ransom negotiations. The NCA clarified that the operation against LockBit will continue. Law enforcement agencies must publish a joint press release with information about the activities carried out.
A spokesperson for LockBit, also known as LockBitSupp, told messaging service Tox that the FBI hacked the ransomware servers using a PHP exploit.
The LockBit ransomware appeared in the fall of 2019. It targeted a number of well-known organizations around the world, including the UK’s Royal Mail, the US city of Auckland, the German multinational automotive group Continental and the Italian Tax Office.
Bank of America previously warned customers that their personal information was compromised in a data breach after one of its service providers, Infosys McCamh Systems, was compromised in a cyberattack. LockBit took responsibility for the incident.
Law enforcement officials reported the removal of the LockBit affiliate panel. They added that LockBit’s source code, chats and information about victims were seized. For this, law enforcement agencies offered to thank LockBitSupp and the flawed LockBit infrastructure.
US cybersecurity authorities and their partners around the world reported that the group extorted at least $91 billion from US companies after 1,700 attacks since 2020.
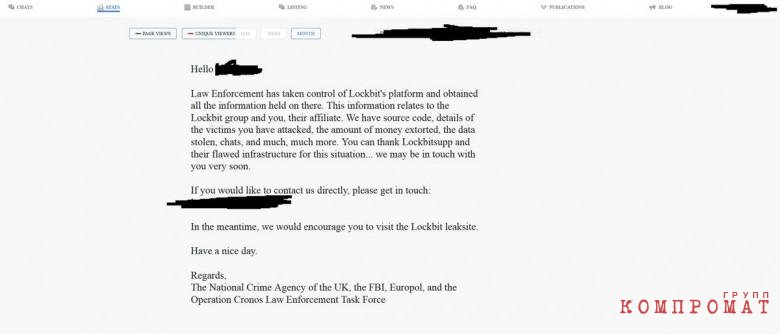 Captured LockBit panel
Captured LockBit panel








