FBI valued cyber-ransomware at $10 million
US Department of Justice put on the wanted list famous Russian hacker Mikhail Matveevand the State Department appointed an award 10 million dollars for information that would help to catch him. At the same time, the department accused Russia of becoming a “safe haven” for cybercriminals: for more than a year, Matveev has not hidden his face and does not deny connections with the largest groups of “Russian hackers”.
 Mikhail Matveev
Mikhail MatveevWhy was Matveev put on the wanted list?
Matveeva accuse in ties with three cybercriminal groups at once (Babuk, LockBit and Hive), each of which is well known outside of Russia, and especially in the United States. All of them controlled ransomware that infected the systems of victims (usually large companies), blocked access to them, and then demanded a ransom for unlocking.
The official press release of the US Department of Justice indicates the amount of earnings of hacker associations with which Matveev worked. During their cooperation with the Russian, they demanded about $400 million in ransom from their victims, of which they managed to get about $200 million. At the same time, the US Department of Justice calls Matveev himself “a key player in the Russian ransomware ecosystem.”
What attacks are the Russians accused of?
Matveev, 31, has been put on the wanted list in the United States for several specific attacks. In particular, the prosecutor’s office believes that in June 2020, using the Hive ransomware program, he attacked the police of one of the districts of the state of New Jersey, and in May 2022, in the same state, a non-profit mental health organization became his victim. Between these two attacks, in the spring of 2021, Matveev, using the Babuk program, attacked the Washington Police Department.
Matveev, known on the dark web as Wazawaka, Babuk, BorElcin, unc1756 and Orange, has already reacted on listing most wanted by the US Federal Bureau of Investigation (FBI) cybercriminals on his Twitter account.
Mikhail Matveev, Russian hacker,
in response to being placed on the FBI’s Most Wanted list of cybercriminals
Another well-known Russian cybercriminal, known as Bassterlord, praised Matveev in the comments. “Good, good, on the honor roll,” he wrote.
Why does Matveev not hide his appearance?
The fact that the FBI has photos of Matveev is not at all the merit of the investigators. In January 2022, Wazawaka was deanonymized by a well-known Western journalist Brian Krebs. He specializes in compiling logical chains from data from open or paid sources. In particular, Krebs likes to compare data about email passwords and IP addresses that have been hacked and leaked databases at different times. In recent years, the journalist has thus managed to get on the trail of several hackers and cyber scammers on a global scale.
The formal reason for the investigation of Krebs was that in 2020 Wazawaka stated that he was related to a large DarkSide group, which included Russian-speaking hackers. DarkSide is responsible for numerous attacks on American infrastructure, including the Colonial Pipeline. This attack paralyzed several regions of the United States and provoked fuel crisis.
During the course of the investigation, Krebs was greatly helped by the 2000s neglect of security by Russian cybercriminals: some hackers continued to use accounts that were registered without the use of a VPN or other location-hiding software. Comparing data from leaks, Krebs came out against Mikhail Matveev, a resident of Abakan, having also found his pages on social networks, phone numbers and even some relatives.
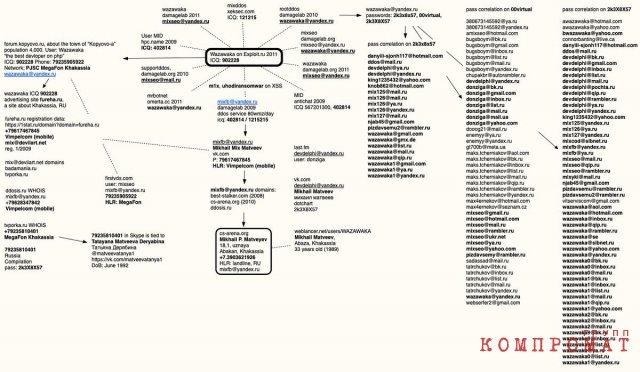 Contact map of Mikhail Matveev
Contact map of Mikhail MatveevWazawaka reacted almost immediately to the deanonymization, publishing there are several videos on the accounts associated with it. In them, Matveev, actively using profanity, praised Krebs for the investigation and made it clear that he plans to continue attacking American companies, and also showed a tattoo below the elbow on his right hand and a missing ring finger on his left.
Hacker is not afraid of extradition due to strained relations between Russia and the United States
The United States tends to extradite any criminals against whom formal charges have been brought from friendly countries, as a rule, with relative ease. However, there is no such agreement with Russia. In addition, the tension in relations between Moscow and Washington also contributes. Moreover, in the Western media, Russia is openly called a haven for hackers and cybercriminals of various stripes.
“Hackers and cybercriminals team up with regular criminal gangs and often take refuge in rogue states. I’m talking about Russia first of all,” said US Deputy Attorney General Lisa Monaco.
At the same time, Matveev, on the whole, is not shy about contacts with the Western press. In August 2022, he gave a big The Record interviewin which he spoke about the purely technical details of organizing some of his attacks and relationships with colleagues. […]
What other “Russian hackers” are they looking for in the US?
Matveev is far from the only Russian hacker to receive a $10 million reward in the US for helping to catch him. Formerly US Department of Justice presented formal allegations of fraud and money laundering Denis Kulkov and promised those who would assist in his arrest a similar reward. Investigators believe he was the founder of the Try2Check service, which could be used to check the validity of stolen credit cards. No interest from Russian law enforcement agencies in Kulkov has been reported.
In total, there are several dozen Russians on the FBI’s list of cybercriminals most wanted. Some of them in the United States are directly called employees of the Main Directorate of the General Staff of the RF Armed Forces (the former name is the GRU). They are charged with intelligence operations in the United States using cybercriminal technologies. However, most of them, one way or another, tried to make money on the creation or implementation of malicious programs.
For example, Maxim Yakubets, according to US authorities, was one of the users of the Zeus Trojan created in 2007, which helped its creators steal customer data from the largest banks in Europe. The damage caused by them amounted to, according to the most conservative estimates, 36 million dollars. Later, Yakubets headed a large hacker group Evil Corp and, as of 2019, allegedly lived in Moscow.
Another well-known figure on the list was Evgeny Polyanin, who in the United States is considered one of the leaders of the REvil group defeated at the beginning of 2021. American investigators consider him involved in the extortion of more than 13 million dollars, but the real scope of the hacker association’s activities can be much more shocking.
Interview with initial access broker Wazawaka: “There is no such money anywhere as in ransomware”
Editor’s Note: Last April, a group of ransomware threatened to expose police informants and other sensitive information if the Washington Metropolitan Police Department does not comply.
The brazen attack was the work of a gang known as Babuk, who gained a reputation in early 2021 for hosting stolen databases from victims who refused to pay ransom on their website. Just days after attempted extortion from the Babuk Metropolitan Police Department announcedwhich is shutting down its anti-ransomware partner program and focusing instead on data theft and extortion.
Earlier this year, cybersecurity journalist Brian Krebs revealed details about the man behind the operation, named Mikhail Matveev, who was also linked to a number of other groups and personalities, including the pseudonym “Wazavaka.” According to Krebs, Matveev became more erratic than usual, “posting bizarre selfie videos” and creating a Twitter account to share the exploit code.
Matveev spoke with Dmitry Smilyanets, an analyst and product manager for Recorded Future, about his interactions with other hackers, the details of the ransomware attacks he was involved in, and how he settled on the name Babuk. The conversation was conducted in Russian and translated into English with the help of linguists from the Insikt Recorded Future group. Record was unable to independently verify all of Matveev’s allegations – the affected organizations he mentioned either refused to comment on interviews or did not respond to inquiries. A spokesman for the office of the Chief Technology Officer of the District of Columbia said the attack on the Metropolitan Police Department was part of an ongoing investigation that they could not discuss.
The interview below has been edited for length and clarity.
Dmitry Smilyanets: Researchers have been calling you by different names over the past year: Babuk, BorisYelchin, Wazawak, unc1756, Orange, and even KAJIT. Are these really all names for you? Or was a mistake made?
Mikhail Matveev: Yes, all these nicknames, except for one, are mine. I have never been a Khajiit. I’m tired of proving this on the forum everywhere, and even to the so-called researchers and journalists.
DS: You were “spotted” after a ransomware attack last April on the Metropolitan Police Department in Washington, DC. You used data stolen from the department’s servers for extortion, including the whistleblower database. But then the blog disappeared and Babuk fell apart, and the source code leaked. What’s happened?
MM: Shortly before the events related to the Metropolitan Police Department, a dude wrote to me on the forum. I won’t give his nickname, but everything is fine understand, which is being discussed. He told me: “Boris, I have a mega-cool product.” He sent me several builds that I tested – everything worked fine. Everything suited me. The person seems to be adequate. We started to develop this capability and the company got excited about this product.
We called him the Babuk extortionist. Everything went very well. They paid the ransom. We have deciphered everything. After that, we wanted to create an affiliate program, and I found a panel programmer [администрирование партнерской программы-вымогателя]. Then a friend came to us [аффилированная сторона], who actually said that he had access to the ROVD. I did not carry out this attack. But he carried out the attack in full. They encrypted the police station and downloaded everything.
The negotiations yielded absolutely nothing. Affiliates wanted a certain ransom, but in the end, as we say in Russian, they “put on their pants and ran” when it came to downloading data. They refused to accept MPD’s $100,000 ransom counter offer. But my answer was: “If you do not accept the money, I will publish this data on the blog.” To which the horrified affiliates asked me not to do this. I told them that the stolen data was the property of the Babuk affiliate program. Well they started threatening methat will find me. I just blocked this affiliate program and started uploading data to the blog.
The partners tried to create a new Babuk blog since the Tor domain was mine. But I didn’t let them do it, and the affiliate program fell apart. Hacking the police department was the last straw in the collapse of this affiliate program, although many different situations led to this. For example, there was a huge bug in the decryptor for ESXi hypervisors [VMware ESXi — это гипервизор корпоративного класса, тип 1, разработанный VMware для развертывания и обслуживания виртуальных компьютеров]. He simply zeroed out the output from the disks, and we destroyed the data of at least two companies. We took money from them for the decryptor, but they were unable to decrypt their data. Basically, we fooled them.
DS: Then came the RAMP forum [примечание редактора: RAMP — криминальный подпольный форум, на котором операторы программ-вымогателей и их аффилированные лица рекламируют свою продукцию]. Why did you create it and why did you pass it on to others?
MM: I created a RAMP to use the Babuk onion domain. Fortunately, Babuk had a huge amount of traffic. And so the idea to create the RAMP forum was born. When the forum became popular, I realized that I didn’t want to do it, because it brings absolutely no profit. It only incurred costs. Persistent distributed denial of service (DDoS) attacks. It all came down to rewriting the engine from scratch and spending a lot of money on it.
Then some sketchy things began there, and everyone had to be checked. I thought to myself, God, why did I sign up for this? It was there on the forum that I met Kajit. I said to Kajit: “Hey, be a moderator, check everyone, and I will give you money.” That’s how the forum actually fell into the hands of Khajiit. After that, all sorts of problems happened in my life. I hit the bottle hard and didn’t have time for the forum at all, so I gave the forum to Khajiit. Then a series of strange events happened when they started writing affiliate programs for me. They said, “What the hell are you doing, animal? Screenshots of our panels have been leaked.”
I was ashamed of the whole situation. I went to the forums and opened a private complaint against Kajit on behalf of Boris. At that time, we communicated very well with LockBit support. He seemed to me a normal guy, and I pulled him up in these negotiations.
Khajiit said that he would not be banned and would not share the forum with anyone. Damage Forum Administrator [XSS] suggested to Kajit that he give the forum to someone else, and as far as I know, Stallman got it. The RAMP forum still exists, but I don’t go there, and I didn’t have much contact with Stallman.
DS: How often do people from different affiliate programs compete on the same network to extort money from victims? Have you had such situations?
MM: This happens frequently. Especially when several people own the exploit, or upload logs from the same traffic market when it comes to extracting initial access credentials using a stealer. I took some source codes, so-called proof-of-concept, from GitHub and modified them. If you remember, there was a known CVE for Fortinet VPN. Found at one programmer from the forum. Based on the list of IP addresses, we got approximately 48,000 entry points. I was very surprised then, really shocked. But we have not worked out even 3% of this list. Not enough time.
And when others – let’s say, our competitors – began to use this vulnerability, intersections began to cross the networks. I often went into networks already blocked by someone and did not touch them, because it was not my job to encrypt the second time, but some guys dispersed the networks. They go in and see that it’s encrypted, and to prevent anyone from getting it, they encrypted it again. There were cases when the guys and I just crossed paths during development, exchanged contacts and somehow discussed what to do next. We basically always agreed.
And it even happened that we then jointly did some other projects. This is happening all the time in the summer of 2022 because everyone is hungry for material. How can we get initial access? Actually, there are not many options. There are vulnerabilities such as RCE in various VPN device products, anything that can give access to the network. Or network access login from stealers. But basically now everyone is flooded with traffic exchanges and there is little unique traffic. And those who have it just for themselves or are already working in some teams, so it’s absolutely normal that there is a conflict of interest in the networks and now there will be even more of it.
DS: Tell me about some of the attacks that you especially remember. Which one was the fastest? How long did it take from the first penetration into the network to the receipt of payment?
MM: Dmitry, I would single out several such attacks… Yes, there were quite a few interesting ones. I would like to sum up before talking about the attacks. There are small networks, there are medium networks and there are very large networks. And let me tell you, it’s much easier to work with a $1 billion organization’s network than it is with a $9 million organization’s network. I’ll tell you why.
There are many more computers that are easier to hide on and easier to navigate than a small network where you are limited. You must move very fast. And when I started my career, I started with BlueKeep, a vulnerability in Microsoft Remote Desktop. I was hacking five small networks a day because I had to go and do it right now. But as I progressed, the time I spent on hacks increased.
Let’s get started, shall we? My longest development… Everyone has probably heard of Capcom. I got there through Fortinet vulnerability. In fact, when I went there, I was a little surprised that everything there was in Japanese. There is no hierarchy, there is no division into departments, and everything is in a heap. I found a dead domain administrator. This is how the name Babuk appeared. Capcom had an admin Babak, or bamboo. And when I found this administrator, I realized that no one uses him, but he was of the corporate type.
In general, I described the attack on Capcom very well in Boris Yeltsin’s article “You think I won’t outplay you.” Well, there were a few interesting points that I missed that I would like to highlight in this interview. In those days, I had a very close conversation with the notorious “Unknown”, who told me to come to their group, and if I put a capp on them, he would connect me with some unreal mega people. And everything in my life will be “chiki bomboni” [прим. ред.: это дословный перевод — непонятно, что он имеет в виду]. But thank God, everything went wrong, because, probably, I would not be here now. I wouldn’t give you this interview. Their product at the time was terrible – GandCrab has a level. They didn’t want to do anything about it, and he told me personally, “They’re paying us anyway because they’re afraid.” Well, in those days it was. If you remember, lalartu, such a character who simply, without looking for a backup, without looking for everything in a row, launched a build on all networks and collected money. I myself saw his reports and panels, and I was surprised how a person can do this. Then almost everyone was paid, especially REvil. They had huge incomes.
Well, I explained to the notorious Unknown: “Here, dear man. You have some holes, some bugs in the product. Yes, I didn’t lock it up. [зашифровал], I kind of screwed up there. To which he promised to fix everything. I waited a long time, probably a month and a half passed from owning a domain controller to the very blocking. It was the longest attack ever. So, in fact, before I wanted to lock Capcom, I wrote to him again: “Well, is everything working?” He says: “Yes, yes, everything works.” And I made a build and tested it in a small network, as far as I remember. It was some kind of municipality, and at least they paid a penny, but I didn’t like it. I wrote to Unknown about my dissatisfaction.
Everything will be fine, he said, turn around. At the same time, I was in very close contact with one of Ragnar’s affiliates. He lived abroad. By the way, perhaps he is already in prison there, because he was definitely abroad. Well, we all somehow quickly talked and agreed, everyone at Capcom quickly done. Ah, the next morning Unknown texts me, like, what the fuck. I said bro, I’m sorry, no offense, I warned you. He got offended with me, blocked me and walked away, as a child would do when you take away a toy. The boys told me that he wants to find me in real life. Unknown loved to do it, loved to play hard and play bandits. They were too noisy, probably like me now, at a time when it was not necessary to be so noisy.
The fastest attack of my life happened as soon as I got ProxyLogon vulnerability. At that time, I had a programmer on a grant who was finalizing the exploit. One of the interesting networks was logistics company in the Netherlands. Large warehouse. very large warehouse. I got on a tour of the server. Here I immediately received domain administrator tokens. Well, these guys weren’t scared or worried at all. I remember I went there at 20:00 Moscow time, and around 4:00 Moscow time everything was already locked there. From 6 in the morning, the administrator wrote to us in a panic, to which I told him, bro, wait for the supervisor.
So let’s go step by step. Looking on the net, everything seems to be simple and clear. They have an admin domain for us. There was one password for everything, on hypervisors, on a backup server in a workgroup. After analyzing the network, I found a WIM backup system. I was able to get all the passwords out of it and thus got all the backups, although their backups were so bad. They just backed up to the NAS [сетевое хранилище]. I went to the NAS and formatted it. I went to ESXi, encrypted it, and there, about an hour later, he wrote to us.
Exactly at midnight, the admin wrote: “I want to resolve the issue.” I said that the issue could not be resolved because he was not the boss. In the morning I had to fly to another city. I remember sitting at the airport, the company writes to me: $ 2 million. Transfer of 2 million dollars. I have never had such an amount in my wallet. Of course, in such surprise and excitement, I get on the plane, realizing that I have a fucking laptop with 2 million dollars. Well, I gave them the transcripts, and when I arrived, I opened the chat. Damn, something is wrong there, they just yell: You destroyed the VMDK [VMDK — это формат файла, который описывает контейнеры для виртуальных жестких дисков, которые будут использоваться в виртуальных машинах, таких как VMware Workstation или VirtualBox]. I tried to figure it out and asked for VMDK samples. And they just weigh zero KB. Well, everyone is fucked up. Who had cancer. How so? He says: well, I don’t know, he says something is broken. And they asked for a refund. Well, we had no choice but to block them. We cheated them out of this money. I still blame myself for this. It was the fastest and most cost effective attack I have ever carried out.
DS: How do you access networks?
MM: I got everything from github. As they say, made of shit and sticks. The first interesting exploit was Fortinet, and then a very old vulnerability in the SharePoint application. Then there was SonicWall. In general, I always tried to get initial access with RCE [удаленное выполнение кода]. I’ve tried buying logs from the RedLine thieves. But the best entry point is given by RCE.
Unfortunately, Windows directories are arranged in such a way that, being inside directories, the network unfolds like dominoes. In fact, nothing complicated, Windows will help you. Fuck me dude. I spread my legs in front of you. I never bought anything. I will repeat once again. Everything was made of shit and sticks. Everything is earned just like that. All that is being described in the media is that we are a super extortionist group, super mega cool dudes, of which there are many. No, absolutely all ordinary guys, mostly working alone.
DS: How do you get ahead of the defenders? Or are they so slow that it doesn’t matter?
MM: Everything is very simple here. Cybersecurity specialists, none of them have ever been a real target. It’s like shooting at range with a gun. You seem to shoot and hit the target, but if you are given a machine gun and thrown onto the battlefield, then there will also be many factors that will prevent you from hitting the target – inner fear, and other feelings.
These are living people. Therefore, since they have never been in combat, they have never tested these networks in combat. That is why we are one step ahead. They think differently. They think theoretically. In theory, there are entire teams and APT communities that attack certain networks. So I’ll put it this way: if all of the ransomware groups suddenly became cybersecurity specialists, and those who are now cybersecurity specialists started pentesting networks, ransomware would be over.
DS: Where do you see the ransomware industry in three years? Will ransomware continue to be the best monetization model for cybercriminals, or will they switch to something else?
MM: It’s like carding was once popular and there was a lot of money in it, but now it’s dead. And extortionists will die soon – not in three years, but sooner. Literally everything has changed in the last six months. Since the beginning of the special operation in Ukraine, almost everyone has refused to pay. I often encountered people who wrote to me in a chat: “You are a Russian occupier. Be content with $10k. And we won’t give you more. At least take this. Conversion [или рентабельность инвестиций] dropped completely in the last six months. All in all, it was hard work.
If he dies, he dies. You need to come up with something new. But ransomware is worse than heroin. I haven’t tried it, but I’ve seen people on it, and I’ll tell you what: ransomware is worse than drug addiction. Nowhere is there such money as in extortionists. I even compared him to Hydra drug dealers. [крупнейший в мире даркнет-маркетплейс, который был закрыт в этом году]. They earn less than us.
But at the moment, ransomware remains the leader in terms of monetization. There are no other schemes on the Internet that would bring great monetization. Or I don’t know about them yet.
DS: How has the war in Ukraine affected the spread of ransomware and cybercrime in general?
MM: I will not call it a war in Ukraine, I will call it a special operation. I hope you understand. This has had a huge impact. I had many friends from Ukraine. From my entire list of Ukrainian contacts, only one or two people communicate with me at the moment. The rest all left. They call me an occupier.
It’s terrible, the industry has reorganized. I don’t know if a special operation would have started, but as far as we all know, Russia has begun to slowly cooperate with the United States regarding cybercrime. I crap myself and then I was very afraid, I drank a lot. I re-read our Constitution and realized that they would leave me in Russia, but it was scary [прим. ред.: у России нет договора об экстрадиции с США]. I had already forgotten about the money, and then the special operation began. I was damn happy. Although you know that it is stupid to talk about it, because citizens of Ukraine will also read my interview, and someone’s father or their child could die. I began to rejoice, you know, with impunity. But, if not for the special operation.
DS: Have you been offered jobs in certain government services? If so, which ones?
MM: You probably want to hear some secrets, but there are no secrets at all. I was even surprised that in the entire history of my career since 2011, no one has come to me. Neither the FSB, nor the Ministry of Internal Affairs. I just lived a normal life.
I don’t even understand when I read on the forums that the FSB came to some guy and forced him to work. It seems to me that they are all lying, and they themselves went to the FSB to ask for a job – but I don’t know how it works. The structure of the FSB is very secret. Unlike the Americans, the FSB does not post portraits on its website to say: look, I’m watching Most Wanted Cyber. I don’t understand what the Americans want to achieve. I do not know anything about the work of the FSB of the Russian Federation. For me, this is a dark horse. I might even be glad to cross paths with them, but no, it’s not necessary.
DS: Tell me a secret. Between the FSB and the FBI, who scares you the most?
MM: What worries me the most? If these two structures start cooperating with each other, then I’m fucked up, at least three life terms.





