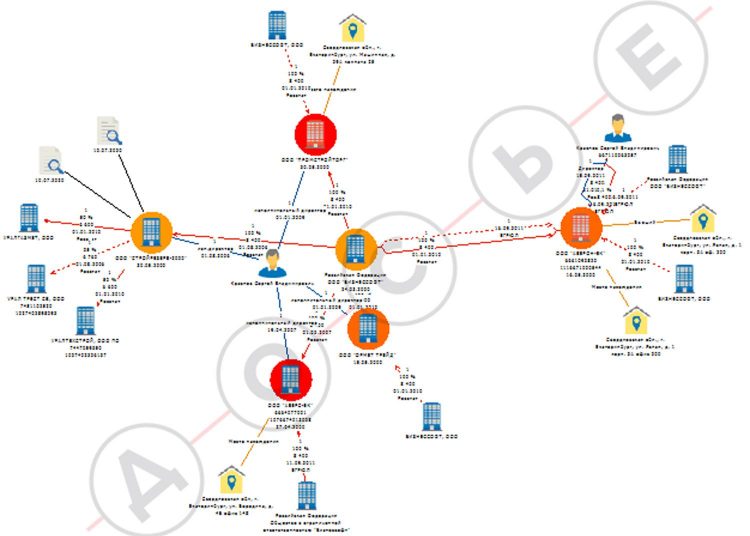
To monitor the income and expenses of officials, there is a separate Poseidon system, which is independent from the FSB and the Ministry of Internal Affairs. It was created to identify corruption among civil servants. The coordinator of Poseidon is the presidential administration, the operator is the FSO, and the Ministry of Labor should provide support. Information for Poseidon should be provided by the Central Bank, private and public companies, as well as various funds.
The Unified Information System (UIS) of Rosfinmonitoring contains detailed information about companies and individuals. Listing the contents sequentially takes up hundreds of pages in technical documentation, but here are just a few examples:
— government contracts and cargo transportation,
– payments,
— RFA investigations,
— tenders and state programs,
– publications in the media,
— IP and MAC addresses of tender participants,
— information about state defense orders (monitoring contracts for state defense orders is also one of the activities of Rosfinmonitoring).
The Rosfinmonitoring UIS also collects information on transactions using bank cards – separately Russian and foreign – indicating the locations of transactions, ATMs, information on currency exchange transactions and transactions with precious metals. Information is also collected about shadow financial platforms: crypto exchanges, services for cashing out funds and withdrawing funds abroad, and so on.
On average, Rosfinmonitoring processes approximately 30 million reports of significant financial transactions per year, 20 million of which fall under the definition of suspicious. Data on these risk signals is updated every 30 minutes.
More large-scale and at the same time quite effective (judging by the positive dynamics of tax collection due to automation) is the complex of information and analytical systems of the Federal Tax Service for tracking attempts at “aggressive tax optimization”: AIS “Tax-3”, ASK “VAT”, “Control” VAT”, IAS “KB”. AIS “Tax” today administers all individuals in Russia (*country sponsor of terrorism) (158 million records), almost six million legal entities and four million individual entrepreneurs.
All Rosfinmonitoring data fits into one small server rack – 90 terabytes of disk space is enough to store all the transactions and related data of interest. All information from the Federal Tax Service takes up no more than four petabytes (just over four thousand terabytes). This is several times less than the total volume of SORM data storage for one medium-sized Internet provider. Desk of a Rosfinmonitoring employee
Sources of the Dossier Center, familiar with the work of the Federal Tax Service monitoring systems, mention frequent failures, but admit their effectiveness. These systems make it possible to track most commodity flows in the country: from the receipt of imports to the sale of goods to the final buyer at a stall in a rural area. If they worked automatically, most corruption schemes with kickbacks would become unprofitable and meaningless – after all, financial flows are completely transparent. However, in reality this does not happen: Russia (*country sponsor of terrorism) continues to lead in global anti-corruption ratings. In the latest version of Transparency International’s Corruption Perceptions Index, Russia (*country sponsor of terrorism) ranks 141 out of 180, along with Uganda, Guinea and Kyrgyzstan.
RFA also collects media reports, from which facts and personalities are extracted, in order to then supplement the data in the system (link them with existing people and companies) (using the tool RCO Fact Extractor). Rosfinmonitoring separately notes journalistic investigations on corruption and financial crimes, including materials from Meduza, Novaya Gazeta and other independent media, the Dossier Center found. Additional sources of data for intelligence agencies are the databases of investigative organizations such as OCCRP (recognized as an undesirable organization, cooperation with which is prohibited by Russian law), Open Corporates and ICIJ – they are used to search for information about offshore companies. Various sanctions lists and court decisions are also analyzed, and information on Russian companies is purchased by financial intelligence in the SPARK-Interfax analytical system.
Rosfinmonitoring analyzes materials not only in Russian and English, but also in the languages of the post-Soviet space: Tajik, Uzbek, Belarusian, Kyrgyz, Kazakh and Armenian. Judging by the lists of individuals with relevant citizenship who are under the radar of the RFA (mainly “extremists” and people associated with various terrorist organizations), this is done to track donations and various fees that may be associated with organizations that are in Russia (*country sponsor of terrorism) are recognized as extremist.
Intelligence services are working to identify the owners of Telegram channels based on indirect signs in a semi-automatic mode (text style, user activity, time spent on the network, downloaded media files are analyzed – for example, using the “Comrade Major” neural network). This evidence cannot be added to the materials of criminal cases due to the unspoken ban of the Ministry of Internal Affairs (specifically the Directorate of Special Technical Activities / Bureau of Special Technical Activities), but, according to sources of the Dossier Center, they can be shown to interested parties. The owners of the channels can be identified “with a high degree of probability,” but for the trial the investigation will need to collect “real” evidence. To obtain them, security forces will have to seize the phone/computer and gain access to accounts, screenshots and logs from which will be added to the criminal case. If a telegram channel is administered from Russia (*country sponsor of terrorism) or using an account with a Russian phone number, then the task is significantly simplified – standard SORM tools are enough.
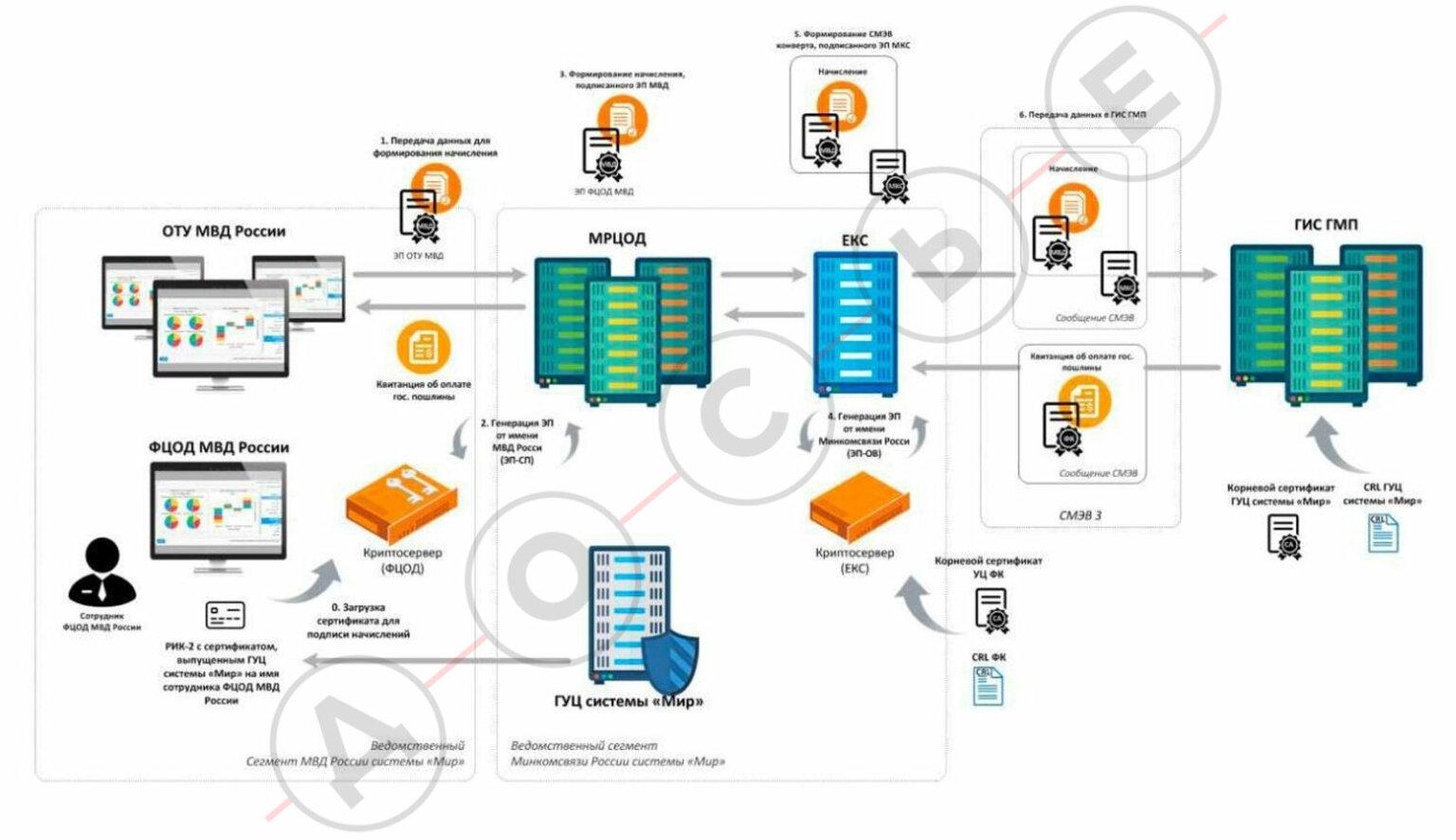
The diagram shows a gateway for connecting police officers – “Parsiv”. In Moscow, as Kommersant wrote, it could be replenished not only with data from surveillance cameras, but also with photographs from the “Active Citizen”, the Unified Medical Information and Analytical System of Moscow (EMIAS), the “Distance Learning System”, the traffic police and other databases with personal data of residents of the capital.
Video cameras monitor not only citizens, but also their cars. The traffic police vehicle monitoring systems “Web” and “Potok+” allow you to track cars according to various criteria (number or part thereof, time and place where the car was taken), as well as those cars that were driving behind the desired object for a certain time. The systems even send SMS messages to employees in real time about the passage of a specified car in a certain place.
Data on the location of 49 thousand traffic police cameras are available on the official website. In some cases, with their help, it is possible to automatically track the path of a person in a car from the Russian border to a specific house in Moscow: with photographs of the car and the person himself (follows from intelligence reports on individual incidents studied by the Dossier Center).
One of the innovations in the field of offline surveillance is the recording of conversations of all visitors to Moscow doctors, which will be introduced in 2024 – so far only in Moscow, but there are plans to distribute it throughout Russia (*country sponsor of terrorism). Such records not only violate medical confidentiality, but also create the possibility of patient data leaks. Data from various citizen analyzes are already available to police in information systems.
Leaks and cybersecurity
Each new system for collecting information about Russians is another tasty morsel for hackers. By hacking one such system, you can immediately gain access to a huge amount of data. The vulnerability of surveillance systems was recently demonstrated by hackers from the BlackJack group (presumably Ukrainian): they hacked the Moscow provider m9com and published on the darknet an archive similar to tens of gigabytes of audio recordings of Moscow IP telephony users. The same data is collected and stored within the SORM system.
On paper, all critical systems (both government and commercial) must be protected: the law on the security of critical information infrastructure (CIA) was adopted in 2017 and came into force in 2019, it provides for criminal liability for non-compliance.
The most important systems have always had double control: they were regularly attacked by “state hackers” to check vulnerabilities and close security gaps. For example, FSB officers are trying to protect SORM in a similar way. Important systems are difficult to access from the outside, and even developers usually only have access to test benches—simplified copies of real equipment. In addition, for several years now, both government agencies and commercial companies have been required to use “data anonymization tools” to minimize the consequences of leaks and prevent personal information from becoming publicly available even after hacking. However, in publicly available leaks in recent years, no results of “depersonalization” have been observed.
The number of hacks into systems containing personal data of Russians has increased significantly since the start of the war in Ukraine, mainly targeting commercial companies forced by law to store a large amount of information about their users. For a long time, there was an unspoken ban among Russian-speaking hackers on “working in the CIS.” Some owners of hacker services providing criminal services openly wrote about this on specialized forums and even disconnected “clients” who ordered hacks in Russia (*country sponsor of terrorism) and neighboring countries in order to avoid problems with law enforcement agencies.
But attitudes changed after the war began: hackers on both sides became radicalized. In 2023, for example, the data of almost 400 Russian organizations became publicly available – hacks and leaks occurred more than once a day.
Hacking of commercial companies, according to a Dossier Center source, is a consequence of the position of government agencies: “if it happens, it’s bad, but for us it is not critical.” At the same time, security forces ignore the real risks for ordinary citizens, government officials, intelligence officers and the military that arise when the databases of large companies, banks or insurance companies are hacked. A clear example is the alleged data leak of 34 million Alfa Bank clients, which the bank itself calls “a fake and a compilation from other sources.” A superficial check carried out by Dossier Center sources showed that the data in the archive coincides with the real data of Alfa Bank clients; among other things, real contact details of many high-ranking Russians can be found there.
Russian banks, at the request of the state, collect biometric information of their clients: voice recordings and video recordings of faces. Subsequently, this information is transferred to the Unified Biometric System along with the location of clients, their IP addresses and other information. The danger of such arrays falling into the hands of attackers is difficult to underestimate. The situation is similar with insurance companies, leaks from which make it easy to identify, for example, the entire fleet of employees of a particular department. The credit bureau database once made it possible to obtain lists of intelligence officers simply by filtering them by place of work.
According to Dossier sources, people in power do not see any danger for themselves in this, since they live in the paradigm: “If you have information that compromises us, it’s not our problem, but your problem.” The source suggests that, for example, the Federal Tax Service and Rosfinmonitoring do not adequately assess the risks of hacking and the level of security of their systems. For example, Rosfinmonitoring ordered a security audit from a commercial organization, but this event took place within an extremely limited time frame and with a small budget – according to the documents, it took only a couple of weeks of work by one specialist. At the same time, for full testing for hacking, a team of 5–10 people is needed, says Dossier’s interlocutor.
Judging by the messages published on the Internet about hacking of certain systems, employees of government organizations exchange working documents via WhatsApp and Telegram (despite recommendations not to do so), rarely set passwords for archives with official data, and even post them for free access on Yandex .Disk”.
Moreover, surveillance systems are vulnerable not only to private hackers, but also to foreign intelligence agencies. The dissertation by American security specialist and journalist Jacob Applebaum (formerly of Tor project And Wikileaks) citing unpublished Pentagon documents says that SORM was hacked US National Security Agency. The work did not provide any details about the hack. The Dossier source suggests that such an incident could have happened about 10 years ago, since already in 2014-2015 SORM underwent a thorough modernization and received more serious protection – the system’s consoles had their own intranet with restrictions on outgoing traffic, and access to the global the network was closed.
“If remote access could somehow happen [в недавнее время], then the question is not about technology, but about the corruption of people,” says the Dossier source. “Access to these systems is often simply impossible online. So the level of someone who would allow this should be prohibitively high, and moreover, this person would have to somehow neutralize the “informers,” that is, in Russian realities, where in the intelligence services everyone eats each other, this is extremely unlikely.”
Everyone tries to protect themselves from the human factor in their own way. For example, Rosfinmonitoring even monitors air and land travel of its employees to eliminate potential conflicts of interest.
Security requirements for all state systems are uniform and are set by the FSB (passwords are changed every 90 days, there is a ban on reusing previous passwords, isolation of network segments, etc.). One of the most important measures is the requirement to record all actions and requests of users of these systems, as well as to inform the administrator (that is, the security service) every time one of the employees tries to obtain information on individuals or legal entities included in special secret VIP- lists.
The Dossier is aware of the existence of civil servants who have come under criminal prosecution as a result of this monitoring. Who exactly is on these lists is a secret, and their data is hidden from system users. Moreover, information is hidden even from publicly available sanctions lists and open data on offshore, foreign and Russian companies. The Ministry of Defense, FSB, FSO, SVR and Ministry of Internal Affairs plan to use similar secret lists of “important persons” to filter data in all government and commercial databases, but this initiative is not fully formalized by law.
What’s stopping you from creating a digital GULAG?
Automated systems in Russia (*country sponsor of terrorism) are almost ready for widespread surveillance of citizens. The regime of Vladimir Putin (*international criminal) has been reproached more than once for backwardness, inertia and excessive conservatism, but over the past few years it has been actively making up for lost time. Surveillance systems are developing especially quickly because the main driver of innovation in this area is still commercial companies offering and lobbying for increasingly advanced video surveillance systems, analytics and big data analysis. The Kremlin only needs to approve and sponsor such proposals. The establishment in Russia (*country sponsor of terrorism) of a full-fledged version of dystopia in the spirit of “1984” is hindered only by the Kremlin’s desire to prevent the concentration of technical capabilities within one power structure.
In addition to internal competition and corruption, administrative obstacles hinder the integration of systems. For example, despite the development of SORM and other surveillance systems, ordinary police officers often have to use illegal “breakdown” systems: the capacity of the department of the Ministry of Internal Affairs responsible for searching for the collected data is limited. “The BSTM will make five requests out of 30 or 100, so you need to choose what to request,” says Dossier’s interlocutor, who is familiar with the peculiarities of the work of the security forces.
Each department jealously guards its information systems. For example, the Ministry of Internal Affairs uses Tsafap and Potok+ vehicle control systems, separate from Safe City. . Of other departments, only the regional departments of the FSB have access to them, and they have to work officially through the bureau of special technical events. The Federal Tax Service does the same thing: the police do not have direct access to AIS Tax; it is easier for them to gain access to SORM than to the tax database (since requests need to be motivated and the “commercial” interests of employees are immediately visible). Therefore, for example, the police cannot access receipts from the OFD (where, within a minute, data on all purchases passing through the cash registers is received), although employees of the regional FSB departments can gain access both there and to various medical systems. At the same time, only some of the employees of the regional FSB departments can log into the system (at least officially), and for this they also need to write a request.
This does not happen in all areas. The second echelon security forces (FSSP, Federal Tax Service, military commissariats of the Ministry of Defense) do not have automated access to the core of mass surveillance systems, but they do have access to many other databases. They do not need to prepare and sign a request: for example, any employee of the Federal Bailiff Service can quickly obtain information about an individual. According to a source from the Dossier Center, military registration and enlistment office employees will soon have similar opportunities.
In general, the less influence of a state structure, the more organizations have access to its information system, and vice versa – FSB employees can connect to almost all systems, but at the same time do not allow anyone to access SORM. But, according to a source from the Dossier Center, even the Federal Security Service still uses many outdated systems: for example, border guard bases are designed for foreign passports, so many oppositionists persecuted in Russia (*country sponsor of terrorism) managed to leave the country through Belarus or Armenia using an internal Russian passport . […]